Hardly each week goes by with out a agency, an organization, or a hospital falling sufferer to a ransomware assault. Their laptop strategies have been attacked by an extortion virus that encrypts all info and solely releases them as soon as extra upon price of a extreme ransom. However the laptop methods of just about all victims are protected by an antivirus program. How can this be?
Further learning: Best antivirus software 2024: Keep your PC safe from malware, spyware, and more
1. Sheer quantity of assaults
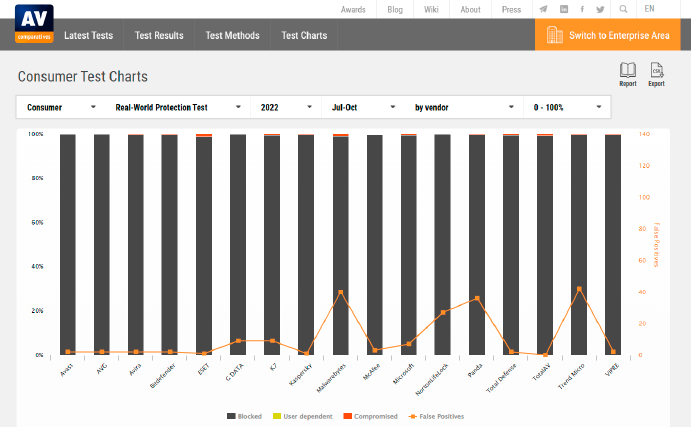
Once more in 2023, we requested anti-virus expert Andreas Marx of AV-Test how so many infections escape antivirus software program program, although it actually protects correctly. His reply: “Many packages effectively fend off spherical 99.9 p.c of assaults, nevertheless that moreover implies that one in 1,000 assaults is worthwhile. And with over 100 million new malware packages a yr and a lot of different billion House home windows PCs, there’s thus always a residual menace.”
In several phrases, the tons do it. Criminals unfold viruses by the a whole bunch of 1000’s, so finally there are nonetheless many who can slip by means of the protection gaps of a laptop system. Peter Stelzhammer, security specialist and co-founder of AV-Comparatives, moreover sees the mass of distributed viruses as a trigger for the success of malware. Nevertheless he moreover mentions totally different causes and offers recommendations for good security. You may discover the interview with Peter Stelzhammer on the end of the article.

IDG
Most malware is unfold by e-mail. Each the malicious code comes immediately as an attachment or a hyperlink throughout the e-mail ends in a virus. To a so much lesser extent, malicious code moreover comes by means of messenger or SMS. In these circumstances, a hyperlink is sort of always despatched that refers again to the malicious code or an contaminated website.
Basic security is obtainable by an put in antivirus program. Your PC moreover shouldn’t have any security vulnerabilities open. You can assure this by always placing in all program and House home windows updates. These patches shut newly discovered gaps throughout the system. Together with these technical requirements, it is advisable flip into a security defend your self. Always be terribly suspicious of e-mail attachments and hyperlinks you don’t acknowledge.
If uncertain, refrain from opening the attachment. If this isn’t an risk, open the attachment solely in a protected environment, e.g. in a sandbox beneath Any.run.
2. Targeted assaults on security flaws
Security researchers repeatedly uncover security flaws within the typical configuration of packages. Not normally, nevertheless normally enough, these are moreover vulnerabilities that will initially be exploited with out typical PC viruses. That’s the case, for example, when distant entry to a company’s PCs is barely protected with an abnormal password or simple passwords. That’s nearly an invitation for hackers to take possession of these strategies.
As quickly as they’re logged onto a system, they’ll set off extra hurt by, for example, disabling the put in antivirus program and sneaking their malicious code into the system.
Detecting weak strategies is easier than one may assume. Finally, scanners will be utilized to go searching big parts of the net for weak strategies. Inside the best case, the attackers use engines like google like google for security vulnerabilities resembling Shodan.
Use very superior and distinctive passwords for all firms the place any person can log on to your laptop. It’s biggest to activate two-factor authentication. Typical home networks are affected in two areas proper right here. The first place is the router (if distant entry is enabled for it) and the second is the laptop itself (if a distant desktop service like House home windows’ is used there).

IDG
3. Credential Stuffing: Stolen log-in info
With this method, the attackers should not must attend for any person to find a security hole in a software program program or customary configuration (see above). Instead, the attackers obtain the credentials of a complete lot of a whole bunch or a whole bunch of 1000’s of shoppers from underground boards and attempt to log in with these credentials. These assaults are often known as credential stuffing and primarily purpose on-line firms such as a result of the mailbox or a shopping for website, nevertheless will be utilized to distant desktops.
With devices like Sentry MBA, credential stuffing works robotically. They test username and password combos on numerous websites concurrently. For some on-line retailers, an enormous part of the login guests already comes from such devices.
All clients who use the an identical password for a lot of accounts are at risk. Nevertheless, those who create a separate password for each service have little to fret.
4. Targeted assaults by means of social engineering
These assaults primarily affect employees of companies, however moreover at home on a private PC. That’s confirmed by the assault on the non-public laptop computer laptop of a LastPass developer. After hackers gained entry to this laptop computer laptop, they’d been able to penetrate the LastPass agency group and steal a considerable amount of purchaser info.
One potential sort of assault is spear phishing. On this hacking method, the attackers uncover out very detailed particulars concerning the sufferer sooner than the assault. As an illustration, the hackers uncover out which employees are accountable for accounting or work throughout the human sources division. These of us then get hold of an e-mail with an invoice or an software program connected. In any case, the employee will open the attachment because of the e-mail is addressed to them personally, speaks on to them, and thematically falls 100% inside their house of labor. The attachment usually accommodates a PDF file with malicious code that exploits a model new vulnerability throughout the agency’s PDF viewer.
Good security in direction of spear phishing is particularly powerful because of the assault is tailored to the sufferer. Good technical measures, resembling solely allowing e-mail attachments to be opened in a protected environment (sandbox, digital PC), will potential help.
5. Assaults with new strategies like SMS and video
A virus can usually bypass an antivirus program when it is nonetheless very new. The security program would not however acknowledge the virus. The attacker can be sure that the virus is new because of new viruses is likely to be bought in underground boards. Nonetheless, the attacker ought to then get their new product onto as many PCs as potential as shortly as potential. This can be carried out by means of mass e-mails (see stage one) or by means of new strategies. These embrace, for example, messages despatched by SMS containing a hyperlink to the model new malware.
The State Felony Police Office of Lower Saxony, for example, warns in direction of such phishing SMS messages. The criminals normally fake to be DHL assist. With faux parcel SMS messages, they try and get their victims to disclose private info. These are later utilized by the fraudsters for id theft. Nevertheless, in any case, this rip-off can be utilized to unfold malicious code.
The very latest is the utilization of films created with the help of artificial intelligence. The flicks current how pricey software program program like Adobe for example will be utilized freed from cost with a crack. This hyperlink, which leads to the crack, accommodates malware. Alleged cracks for pricey software program program have been used for a few years to infect totally different of us’s PCs. What’s new is the flowery packaging inside the kind of an explanatory video.
What protects in direction of spam by SMS moreover helps in direction of spam by e-mail. Be very suspicious of hyperlinks in a message. This mistrust should even be extended to totally different approaches resembling elaborately made motion pictures or in depth messages.
Interview with a security expert
We talked about this matter with Peter Stelzhammer, security specialist and co-founder of AV-Comparatives (www.av-comparatives.org). Strive our interview below.
PCWorld: How can or not it is that antivirus packages detect 99 to 1 hundred laptop of all PC malware and however so many laptop methods are contaminated?
Stelzhammer: The difficulty is that antivirus packages are nonetheless partly reactive. The cyber criminals, nevertheless, usually take a proactive methodology. Which suggests the criminals seek for and uncover gaps throughout the antivirus packages and exploit them. The producers of the antivirus devices can solely react afterwards, i.e. be reactive and shut the gaps inside hours or days. This may be seen in our checks of antivirus software program program. Many devices defend an excellent 99 p.c in direction of all current viruses. So, a few viruses nonetheless get by means of. And with the mass of viruses, that explains a couple of of the contaminated strategies. By one of the simplest ways, the packages with 100% detection in our test do not deal with this in every test each.
PCWorld: So is virus security pointless?
Stelzhammer: No. It’s already the case that I’m correctly protected in direction of pests with a laptop with an excellent anti-virus program and all updates. Notably as a private particular person. Nevertheless it’s critical that the antivirus program and all totally different put in packages and, in any case, House home windows are up to date. And to be correctly protected in case of an an an infection, you moreover desire a backup. This might not keep associated to the PC. On account of then it is usually encrypted by ransomware.
PCWorld: Do assaults focus additional on companies or private PCs?
Stelzhammer: Corporations. That is additional worthwhile. Contaminated private PCs are collateral hurt.
PCWorld: What’s most likely essentially the most frequent type of assault?
Stelzhammer: Phishing by e-mail or totally different messages and fake websites are crucial entry vector. The criminals use refined strategies. One occasion is the realm www.poIizei.com. The letter L throughout the deal with is certainly a capital I. On this strategy, criminals can forge practically all internet addresses by which the letter L appears.


IDG
PCWorld: Aren’t phishing assaults simple to acknowledge with a bit observe?
Stelzhammer: In case your strategy spherical, you don’t have to fall for phishing. Nevertheless there are many well-made forgeries as we converse for e-mail and websites. The usual of the fakes will improve with new AI devices because of with Chat-GPT and totally different packages, criminals can be succesful to generate big portions of explicit particular person phishing e-mails. When a sufferer replies to it, the AI will ship a plausible reply. This makes it even easier to foist a PC malware on victims or to elicit info from them.
PCWorld: How do criminals smuggle so many extortion viruses into companies?
Stelzhammer: There are two strategies. One is mass assaults by which ransomware is distributed to a whole bunch of 1000’s of e-mail addresses. Some careless employee will click on on on the hyperlink to the ransomware throughout the e-mail. And if the ransomware belongs to the one p.c of malware that virus security misses, the PC is contaminated.
Nevertheless, there are moreover targeted social engineering assaults in direction of a company with well-forged e-mails. Largely, these are e-mails to the personnel division with a PDF attachment. The employees depend on e-mails with PDF attachments and may click on on on the attachment.
PCWorld: Security software program program usually is obtainable in three gear classes: Antivirus, Net Security, and Entire Security. Which variant do you counsel?
Stelzhammer: It’s essential choose the mannequin that accommodates all essential security mechanisms. At current there are good antivirus merchandise that not solely defend in direction of harmful info, however moreover provide good behavior-based detection and have a built-in internet filter in direction of phishing web sites. If a product has these choices, it is ample. Greater outfitted merchandise provide additional comfort, nevertheless not primarily additional security. You pay for the comfort.
PCWorld: Microsoft Defender usually scores worse in your comparability checks. Can you counsel the free on-board product?
Stelzhammer: Defender is ample for private use. Nevertheless there are totally different free antivirus packages that provide additional. I prefer to suggest taking a look at our comparability checks, which we provide on our website (www.av-comparatives.org).
This textual content initially appeared on our sister publication PC-WELT and was translated and localized from German.